FormGrabber
Almost every sensitive information, such as passwords, login credentials, bank account numbers, credit card numbers, etc, is sent from your web browser when you fill an online “form” to a secure remote sever trough the web standard HTTPS POST.
A form grabber is a malicious code that intercepts POST data coming from web “forms” before the encryption takes place, thus avoiding the added security of the https protocol.
Our FormGrabber
- We have successfully implemented a form grabber that grabs all POST data and sends it to a remote server for a later use.
- Our form grabber runs within Firefox. This means, it should be possible for our “standard citizen form grabber executable” to gain Firefox’s privileges.
- It is present in RAM so no traces are left. The next time Firefox is launched, our form grabber disappears.
- It is not currently detected by antivirus software.
Our implementation is based on the work of “The Anomaly”. The original code may be found here. We mainly commented and fixed the code to make it compatible with the latest Firefox releases.
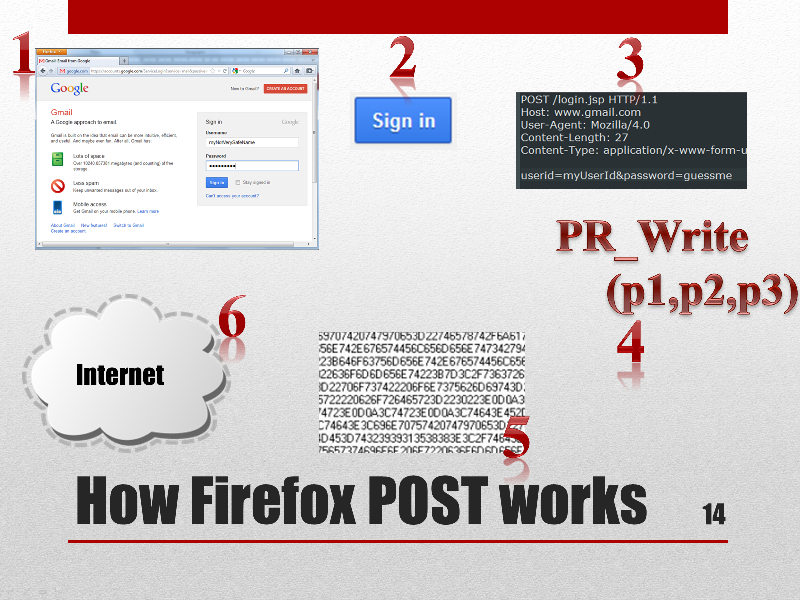
How does it work ?
Firefox Internals
When a user access a remote site such as gmail.com. He completes a form with his email address and password. When he hits the Sign in button, the web browser runs a set of predefined algorithms and builds what will be the final HTTP request. These request will be encrypted and later sent to a remote server through the Internet, becoming an HTTPS request. All this work is accomplished by a function named PR_Write, which receives 3 parameters:
- The first is a socket file descriptor and is not very useful to us.
- The second is a string pointer aka “char *” to the data that will be sent to the server.
- The last parameter is the size of the data.
The goal of our form grabber is to grab the second and third parameters of this function each time it is called, check whether it is a POST request and if so then send a copy of the data to a remote evil server. This function is called both for HTTPS and HTTP requests. (And probably for many other protocols too).
Coming up next : code injection.